CMAC (Cipher-based Message Authentication Code) is a symmetric-key cryptographic algorithm that produces a fixed-size authentication tag (usually 8–16 bytes) for a message. It proves two things:
- Integrity: the message was not tampered with.
- Authenticity: the message came from someone who knows the shared secret key.
It is defined in NIST SP 800-38B (Recommendation for Block Cipher Modes of Operation: the CMAC Mode for Authentication) and is based on a block cipher like AES (AES-CMAC is the most common variant).
Key properties compared to similar algorithms:
| Algorithm | Key Type | Base Primitive | Variable-length safe? | Common Use Cases |
|---|---|---|---|---|
| CMAC | Symmetric | Block cipher (e.g. AES) | Yes (built-in) | Protocols needing block-cipher-based MAC (EMV payments, some IoT, secure elements) |
| HMAC | Symmetric | Hash function (e.g. SHA-256) | Yes | Most internet protocols (JWT HS256, TLS, OAuth) |
| CBC-MAC | Symmetric | Block cipher | Only for fixed-length | Legacy systems (CMAC fixes its flaws) |
CMAC is especially useful when you already have a block cipher (AES) in your system (e.g. for encryption) and want a MAC without introducing a separate hash function.
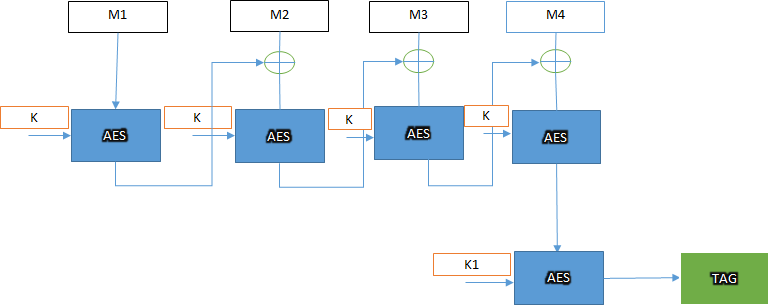
How CMAC Works (High-Level)
- Key: A symmetric block-cipher key (e.g. 128-bit AES key).
- Subkey generation:
- Encrypt an all-zero block with the cipher → Rb.
- Derive two subkeys K1 and K2 by left-shifting and conditional XOR with a constant (multiplication in GF(2¹²⁸)). This is done once per key.
- Message processing:
- Split the message into blocks.
- Run standard CBC-MAC (chain encryption with XOR).
- For the last block:
- If the message length is a multiple of the block size → XOR K1.
- Otherwise → pad to full block, then XOR K2.
- The final ciphertext block is the MAC tag (often truncated).
This subkey trick makes CMAC secure for arbitrary-length messages (unlike plain CBC-MAC, which is only safe for fixed-length).
Relevance to Identity & Credential Systems
In your domain (certificates, identity, credentials):
- Digital certificates (X.509) usually use asymmetric signatures (RSA/ECDSA) for public verifiability.
- Symmetric MACs like CMAC appear when:
- A shared secret exists (e.g. device-to-server mutual authentication).
- Hardware security modules (HSMs) or secure elements use AES-CMAC.
- Payment/contactless cards (EMV) use AES-CMAC for transaction authentication.
- Some IoT credential bootstrapping or attested credentials in constrained environments.
- Protocols that already use AES encryption and want a matching MAC without pulling in SHA-2.
If your system ever handles symmetric-key protected credentials or needs to authenticate data inside a secure channel, CMAC is a standard choice.
(c) from crypto stack exchange