the P71
P71 Card/Chip Overview
The "P71" refers to NXP Semiconductors' SmartMX3 P71 series (e.g., P71D321, P71D320), a family of secure microcontrollers designed as the core chip in modern smart cards. It's one of the most widely used platforms for high-security applications, especially in identity and credential systems like yours.
In your field of certificates, identity, and credentials, the P71 is highly relevant: it's the hardware foundation for many national eID cards, ePassports, driver's licenses, health cards, and PIV-style enterprise credentials. It securely stores private keys, X.509 certificates, biometric data, and executes cryptographic operations for authentication, signing, and access control—all while resisting physical and logical attacks.
How It Works
- Hardware Architecture
The chip features a secure RISC CPU with dedicated crypto coprocessors (Fame3 for RSA/ECC, AES/DES engines, PUF for unique device keys, TRNG for randomness). It includes tamper-resistant sensors (light, voltage, glitch detection) and IntegralSecurity 3.0 countermeasures against side-channel and fault attacks. Memory options reach up to 500 KB non-volatile (Flash/EEPROM) for code/data, plus RAM. Dual-interface support covers contact (ISO 7816) and contactless (ISO 14443 Type A, up to 848 kbit/s). - Software/OS Layer
It typically runs JCOP4 (NXP's Java Card OpenPlatform implementation): Java Card 3.0.5 Classic + GlobalPlatform 2.3. This allows multiple independent applets (e.g., one for eID authentication, one for qualified electronic signature, one for payment/EMV). Applets are post-issuance loadable and deletable in secure ways. - Key Security Features
Certifications include Common Criteria EAL6+ (highest for smart card OS), EMVCo, FIPS 140-3 on some configs. It supports protocols like PACE-CAM (for contactless privacy), EAC (Extended Access Control for biometrics), BAC/SAC for ePassports. - Why It's Common in Identity Systems
Governments choose it because it balances performance (<2s for ePassport SAC), large memory for multiple certs/data groups, and proven resistance to attacks. Over 7 billion SmartMX chips have shipped globally.
Here's a simplified block diagram of the architecture:
Practical Examples
Real-world cards using P71/JCOP4:
- Many modern eID cards (e.g., Slovenian eID uses P71 with JCOP4).
- Some fuel/loyalty cards in Africa (dual-purpose with payment + ID).
- Enterprise PIV cards (US gov-compatible) and FIDO2 security keys.
Here are photos of actual cards built on this chip:
Quick Practical Check: Identifying a P71 Card
Most JCOP4 P71 cards return a distinctive ATR (Answer To Reset). Example from a real Slovenian eID:
3B D5 18 FF 81 91 FE 1F C3 80 73 C8 21 10 0AYou can detect it in software like this (short Python snippet using pyscard – great for testing in credential systems):
from smartcard.System import readers
from smartcard.util import toHexString
r = readers()
if not r:
print("No reader found")
else:
reader = r[0]
connection = reader.createConnection()
connection.connect()
atr = toHexString(connection.getATR())
print("ATR:", atr)
# Typical P71/JCOP pattern starts with 3B ...If you see an ATR starting with 3B … FE 45 … or similar with "JCOP" in historical bytes, it's very likely a P71-based card.
Next Step Connection
When working with certificates on these chips, you'll often deal with EF.CV certificates in the eID applet (e.g., authentication cert, signing cert, QES cert). The secure storage and on-card key generation make them ideal for verifiable credentials—private keys never leave the chip.
Let me know the next term or how this ties into your current project!
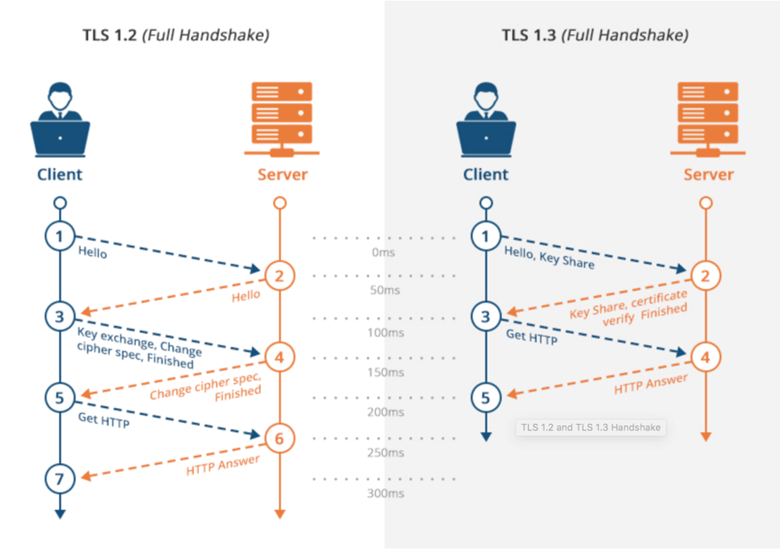

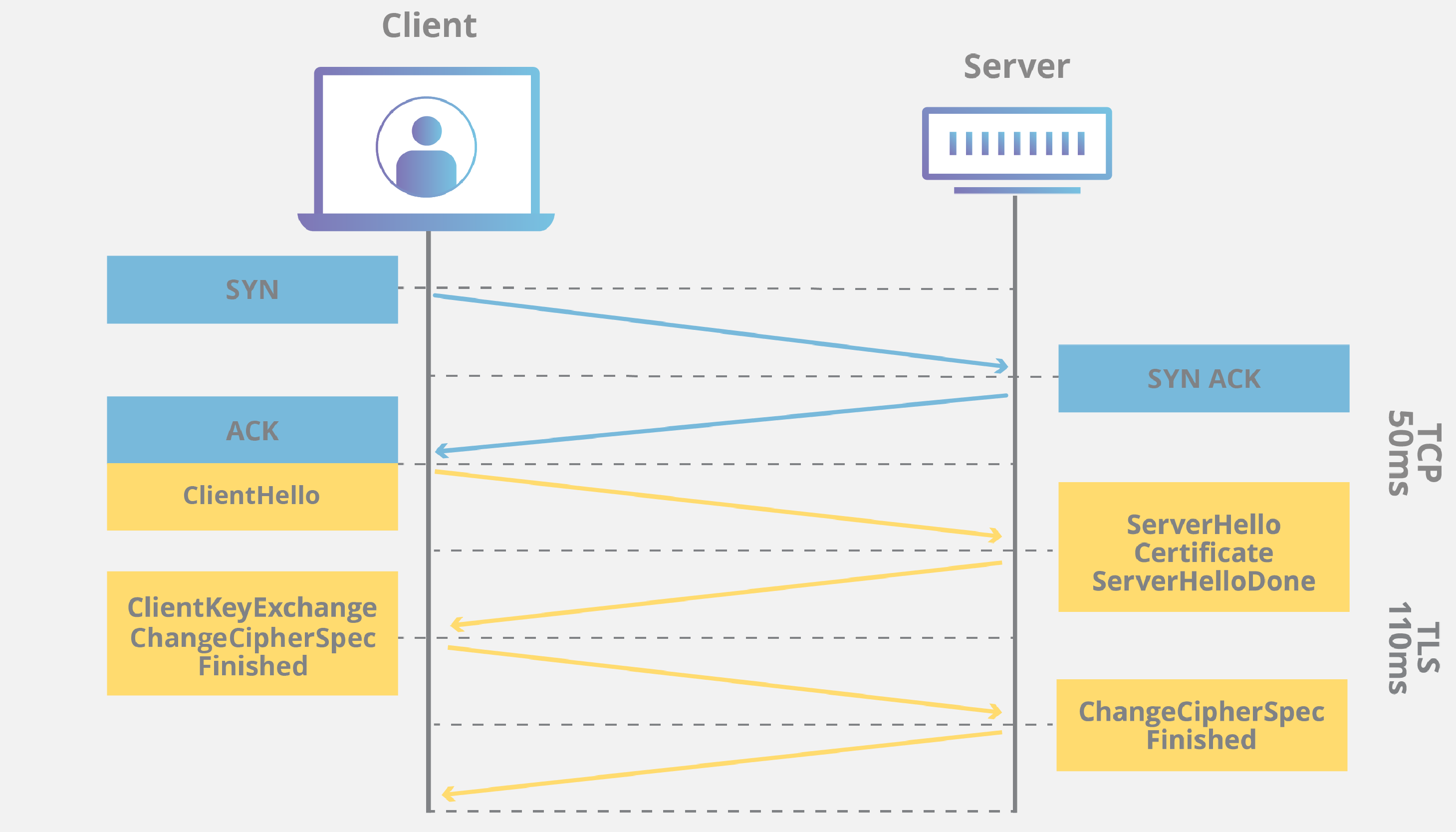
Recent Comments